1. Introduction to security of the information systems
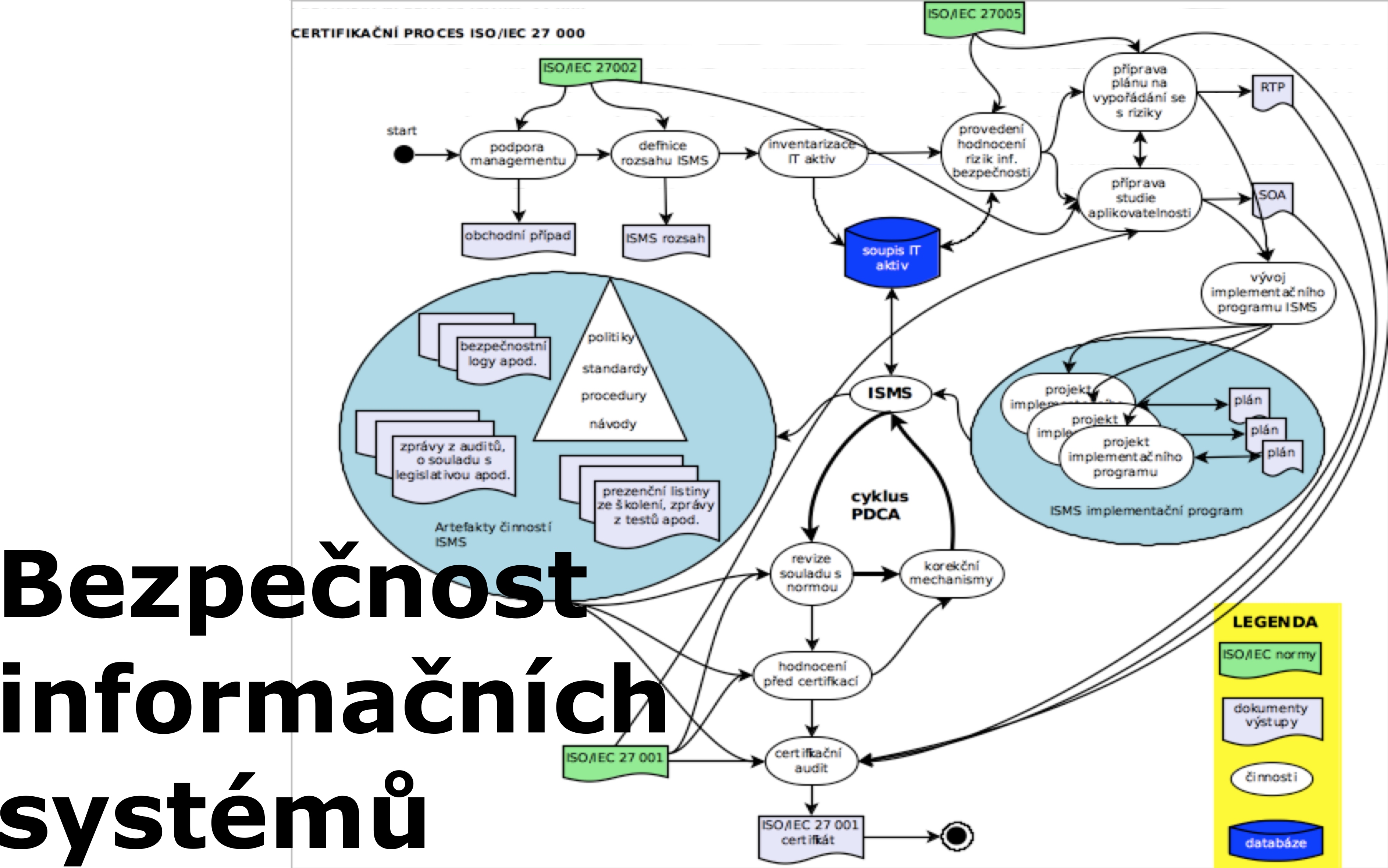
2. ISO 27 000 - ISMS
3. IT Security politics of the organization
4. Risk management for IT systems
5. Configuration management
6. Case studies of the ISO 27 000 documentation
7. COBIT standard
8. ITIL standard
9. Software support for IT security management
10. Anatomy of security incident
11. Forensic analysis of the PC
12. Forensic analysis of mobile devices
13. Current security threats in IT and their connection IT security management
2. ISO 27 000 - ISMS
3. IT Security politics of the organization
4. Risk management for IT systems
5. Configuration management
6. Case studies of the ISO 27 000 documentation
7. COBIT standard
8. ITIL standard
9. Software support for IT security management
10. Anatomy of security incident
11. Forensic analysis of the PC
12. Forensic analysis of mobile devices
13. Current security threats in IT and their connection IT security management